A famed expert Jens ‘Atom’ Steube, created a new WIFI hack that allows the cracking of WiFi passwords on modern routers.
Jens ‘Atom’ Steube, a leading developer of the famed cracking tool Hashcat. The expert has devised a new hacking technique that provides cracking for W-Fi passwords in the most modern and advanced routers.
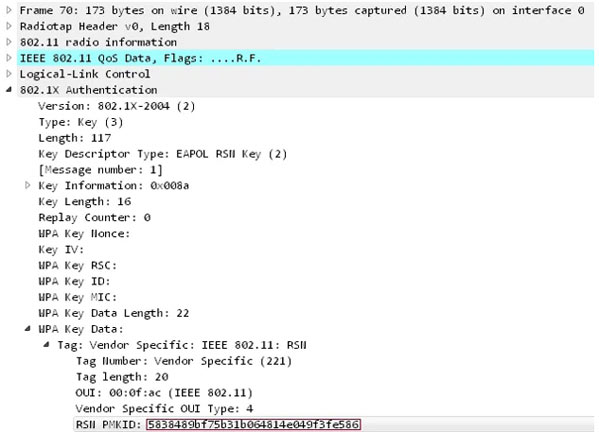
The techniques work against the Pairwise Master Key Identifier (PMKID with WPA/WPA2 wireless network protocols when roaming features are enabled.
The researcher detected the attack he carrying out risk-assessment of the WPA3 security standard. The cracking technique the recovering of Pre-shared Key (PSK) login passwords by the attacker and, in turn, exploits them to monitor your internet traffic as well as hack into your WiFi network.
These new hacks (example of one of the latest tools) are different from other hacking techniques as it doesn’t need the capturing of complete 4-way authentication handshake of EAPOL.
But instead, it uses RSN IE (Robust Security Network Information Element) to request an access point from a single EAPOL.
“The new attacks were accidentally stumbled upon during the devising of various ways of attacking WPA3 security standard. WPA3, which was nearly impossible due to its modernized protocols known as SAE “Simultaneous Authentication of Equals.”
The RSN protocol provides for the establishment of secure communication over the 802.11 wireless network, which employs a PMKID key to create a connection between access point and client.
A detailed guide of attack steps
Step 1- Run the hcxdumptool requesting PMKID from Access Point and dumping of the received file frame normally in pcapng format.
$ ./hcxdumptool -o test.pcapng -i wlp39s0f3u4u5 –enable_status
Step 2- Run the hcxpcaptool tool, which converts the seized data from the pcapng format to a hash format compatible with Hashcat.
$ ./hcxpcaptool -z test.16800 test.pcapng
Step 3- Launching of Hashcat for versions 4.2.0 or higher, a password-cracking tool that does the trick. The Hash mode used for this step is 16800.
$ ./hashcat -m 16800 test.16800 -a 3 -w 3 ‘?l?l?l?l?l?lt!’
Following this meticulous and detailed steps makes it easy to retrieve WiFi passwords from targeted networks
In conclusion, Steube ‘At the time, they didn’t know the exact number of routers or vendors which the new hack works on. But the new technique works like a charm against all 802.11i/p/q/r networks whose roaming functions have been enabled.’
Benefits of this attack
- No need to wait for a complete 4-way handshake between AP a regular user.
- No retransmissions of EAPOL frames
- No invalid passwords sent by the regular user
- No losing of EAPOL frames when the AP or regular user is far from the attacker
- No requirement of replay counters values of fixing of the nonce
- No more specialized output formats- the final data appears as a typical hex-encoded string
- No more need for regular users due to direct communication from the attacker to AP.
